|
Summary
This contribution provides
a high-level description of the process by which
risk management can be carried out. Two models are
overviewed: “Risk Management Guide for Information
Technology - NIST SP 800-30”, and ISO/IEC
27005:2008, Information technology - Security
techniques -Information security risk management.
1. Introduction
The explosive growth in the use
of the information and communication technologies (ICT)
infrastructure has increased the reliance of
organizations and individuals on the protection of
the information transmitted and stored over
telecommunications networks.
This has led to a heightened
awareness of the need to protect the
-
Confidentiality of information
by ensuring that information is accessible only to
those authorized to have access;
-
Integrity of the information by
safeguarding the accuracy and completeness of
information and processing methods; and
-
Availability of information by
ensuring that authorized users have access to
information and associated assets when required.
To meet these security
objectives, organizations practice safe security
techniques based on specialized methodologies to
manage potential risks.
Security risk management plays a
critical role in protecting an organization’s
information from security risk and it is defined as
the logical and analytical process of identifying
risk, assessing risk, and taking steps to reduce
risk to an acceptable level. Security risks are
managed by:
-
Analyzing and assessing threats
and risks to which sensitive information and
assets are exposed;
-
Selecting risk-mitigation
safeguards; and
-
Developing and testing
contingency and business resumption plans.
Managing security risks means
defining what is at risk, the magnitude (impact) of
harm caused by a threat, the causes or events with
the potential to cause harm to an ICT
infrastructure, and what to do about the risk. A
threat and risk assessment is one means to manage
risk. Other means of managing risk would be
education and awareness, security policies,
operational standards, and technical documentations.
The following section provides a
description of risk management approaches in general
as well as applications to manage potential
security’s risks.
2. Risk Management Overview
A number of Risk Management
Frameworks are available in the open literature.
Although these frameworks, and processes defined
within them, differ in detail, there is considerable
overlap in the material covered.
The following themes recur [1],
[2], [3], [4], [5], [6], [7]:
a) Identification of critical
assets
As it is not cost-effective to
protect all assets, it is essential that the
critical assets be identified so that particular
care may be taken to protect them. The designation
should be made from the business context, through
consideration of the impact of the loss or
degradation of an asset on the business as a whole.
b) Identification of risks
A disciplined, comprehensive
identification of risks should be undertaken. It
should include environmental risks, as well as those
caused by humans. The “accidental insider” group
includes human error as well as accidental
misconfiguration conducted by inadequately trained
personnel. When people are the threat, the analysis
should include who they are, their motivation for
threatening the system, and the means by which they
would attempt to achieve their goals.
c) Impact Assessment
It is necessary to relate each
risk to one or more of the architectural components
and determine the potential impact of the threat on
the asset..
d) Treatments
This activity involves planning
and implementing the best course of action:
accepting the risk as it exists today; actively
managing the risk; watching for changes in risk
characteristics (and modifying the plan as needed);
and investigating more about the risk until enough
is known that one of the others planning options
becomes appropriate.
e) Reporting
Who needs to know about the
risks? Who needs to know about incidents? Who needs
to know about threats that succeed?
f) Information Sharing
What information should be
shared? How should the sharing occur? What are the
restrictions on sharing (e.g., should the data be
anonymized before sharing?)
g) Monitoring/Audit
Is there a need for internal
audits? Is there a need for third-party (external)
auditors? Do the regulators require audits? Do the
shareholders require audits?
h) Regulatory/Legislative
What is the regulatory
environment? What laws need to be followed? What
security requirements are imposed by external
bodies?
3. Security Risk Management
Process
Information security risk
analysis/risk management methods usually support the
general concepts specified in ISO/IEC 27000
standards [4] and are designed to assist all types
of organizations in the satisfactory implementation
of information security based on a risk management
approach. The following sub-sections describe a risk
management process followed for an overview of
security risk management guidelines.
3.1. Risk Management Guide
for Information Technology - NIST SP 800-30
The NIST approach [5] involves a
three-step process: risk assessment; risk
mitigation; and evaluation and assessment.
Risk assessment
This process allows determining
the level of the potential threat and their risks
associated with an ICT system. The risk assessment
process includes:
-
System characterization:
establishes the scope of the risk assessment
effort and provides information essential to
defining the risk.
-
Threat identification:
identifies the potential threat-sources that could
exploit system vulnerabilities:
i. Human: unintentional acts
(e.g., inadvertent data entry), or deliberate
actions (e.g., network based attacks, malicious
software upload, or unauthorized access);
ii. Natural: floods,
earthquakes, electrical storms; and
iii. Environmental (e.g.,
long-term power failure).
-
Vulnerability identification:
identifies the system vulnerabilities (flaws or
weaknesses) that could be exercised by the
potential threat-sources.
-
Control analysis: specifies the
controls used for the information system to
mitigate the probability of a vulnerability and
reduce its impact. Examples of effective security
or risk reduction controls are:
i. technical controls
incorporated into computer hardware, software, or
firmware, and nontechnical controls such as
security policies; operational procedures; and
personnel and environmental security;
ii. preventive controls, e.g.,
access control enforcement, encryption, and
authentication; and
iii. security requirements
checklist to be used to validate security
compliance/noncompliance.
i. threat-source motivation and
capability;
ii. nature of the
vulnerability; and
iii. existence and
effectiveness of current controls.
-
Impact analysis: prioritizes
the impact levels associated with the compromise
of an organization’s information assets based on a
qualitative or quantitative assessment of the
criticality of those assets. In this step it is
necessary to relate each risk to the architectural
components and determine the potential impact of
the threat on the asset, and subsequently,
establish the magnitude of the impact (High,
Medium, or Low) resulting from a successful
threat.
-
Risk determination: measures
the level of risk to the information system. It is
expressed as a function of the
i. probability of a
threat-source;
ii. magnitude of the impact;
and
iii. capability of security
controls for reducing or eliminating a risk.
-
Control recommendations:
provides input to the risk mitigation process and
are the results of the risk assessment process.
The goal of this step is to reduce - to an
acceptable level - the level of risk to the
information system and its data. A cost-benefit
analysis should be conducted to demonstrate that
the costs of implementing the recommended controls
can be justified by the reduction in the level of
risk.
-
Results documentation:
describes the threats and vulnerabilities, risk
measurements, and recommendations for control
implementation by documenting them in an official
report. Its purpose is to help in the process of
making decisions on policy, procedural, budget,
and system changes to reduce and correct potential
losses.
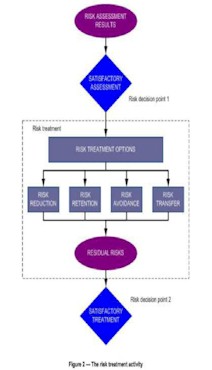
Risk mitigation
Risk mitigation is a systematic
methodology to reduce risk. It involves
prioritizing, evaluating, and implementing the
appropriate risk-reducing controls recommended from
the risk assessment process. The implementation of
the best course of action may vary depending on the
organization.
There are four risk mitigation
options:
1. Risk retention: to
accept the potential risk and continue operating, or
to implement controls to lower the risk to an
acceptable level
2. Risk avoidance: to
avoid the risk by eliminating the risk cause and/or
consequence
3. Risk reduction: to
limit the risk by implementing controls that
minimize the adverse impact of a threat exercising a
vulnerability
4. Risk transference: to
transfer the risk by using other options to
compensate for the loss, such as purchasing
insurance.
After identifying the possible
controls and evaluating their viability and
effectiveness, a cost-benefit analysis to determine
which controls are appropriate to allocate resources
is conducted. Its purpose is to demonstrate that the
costs of implementing the controls can be justified
by the reduction in the level of risk.
The cost-benefit analysis
encompasses:
-
Impact of implementing the
controls (new or enhanced);
-
Impact of not implementing the
controls (new or enhanced);
-
Costs of the implementation:
hardware and software, policies and procedures,
personnel and training, and maintenance;
-
Costs and benefits against
system and data criticality.
Once the cost of implementation
has been established and by comparing their results,
it can be decided whether or not to implement the
risk control measures.
Evaluation and Assessment
The network (components and
software applications), personnel and security
policies are likely to change over time. These
changes mean that new risks will rise and risks
previously mitigated may again become a concern.
Thus, the risk management process continues with the
identification of new or re-emerging risks for as
long as the infrastructure activity or business
process is ongoing.
In evaluating this process the
following actions are available:
-
Continue the current plan
option - when data indicates the risk is under
control;
-
Invoke contingency - when the
original plan did not work as expected;
-
Re-plan - go back to the
planning step and change course; or
-
Close the risk - when the
risk's probability and/or potential impact is zero
or very low.
The next section describes a
security risk management guideline based on the ISO/IEC
27005 standard which intends to provide fundamental
contributions to the well being and security of any
organization.
3.2. Security Risk
Management Guideline
The Security Risk Management
guideline described below is based on the ISO/IEC
27005 standard [4] which intends to provide
fundamental contributions to the well being and
security of any organization. This guideline creates
an ongoing process that drives the organization
towards to effective controls to mitigate security
risks. The follow general practice references many
industry accepted standards for managing security
risk and incorporates the first three phases of the
risk management process described before.
First phase: Risk Assessment
Steps in this phase include
planning, data gathering, and risk prioritization.
Risk prioritization involves qualitative and
quantitative approaches to provide reliable risk
information within reasonable trade-offs of time and
effort.
Second phase: Risk Treatment
Options
During this phase it is
determining how to address the key risks in the most
effective and cost efficient manners. The control
solutions to be implemented are defined after an
evaluation of all the recommended controls,
estimated costs, and degrees of risk reduction are
measured. The output of this phase is a clear and
actionable plan to control or accept each of the top
risks identified in the Assessing Risk phase.
Third phase: Treatment
Evaluation
During this phase it is created
and executed plans based on the control solutions
that emerged during the decision support process to
measure the effectiveness of the program. When the
previous phases of the security risk management
process are complete, organizations estimate their
progress with regard to security risk management as
a whole.
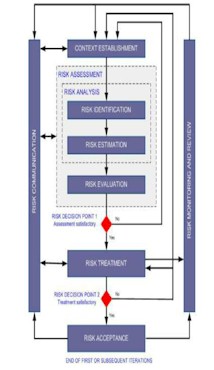
The follow flowcharts (from ISO/IEC
27005) provide a brief of the information Security
Risk Management phases described above.
Figure 1. Risk Management Process
(ISO/IEC 27005)
Finally, the most important keys
for implementing a successful security risk
management program will build on:
-
Management’s commitment and
full support and participation of the ICT teams;
-
The expertise to apply the
security risk assessment methodology to a specific
site and system, identify mission risks, and
provide cost-effective protection;
-
The awareness and cooperation
of members of the user community; and
-
An ongoing evaluation of the
ICT-related mission risks.
4. Summary
This contribution provides
Security Risk Management input to the Technical
Notebook on Cyber security. It provides a high-level
description of the process by which risk management
can be carried out. Two models are overviewed: “Risk
Management Guide for Information Technology - NIST
SP 800-30”, and ISO/IEC 27005:2008, Information
technology - Security techniques -Information
security risk management.
It is recommended that the Cyber
security Rapporteur of the Working Group on Policy
and Regulatory Matters to consider incorporating
this contribution in Chapter 3 of the Technical
Notebook of Cyber Security.
Oscar Avellaneda &
Magdoly
Rondon
Industry Canada
|