|
In the process of identifying mainly unauthorized
transmissions, the following techniques or methods can be used:
geolocation and verification of transmissions, which are the most
widely accepted and valid for satellite operators to identify the
source generating these transmissions.
1. Geolocation
It is a technique that makes it possible to
geographically locate a terrestrial station that is emitting a
transmission to a specific satellite, whether an unauthorized
transmission or, in general, some interference associated with
breakdowns in station equipment or human error.
The result of this geolocation is generated in
terms of latitude and longitude with an accuracy that is typically
under 10 km, that is, the terrestrial station that is transmitting the
geolocated signal is generally less than 10 km away from the
coordinates obtained in the geolocation process.
This technique was scientifically developed more
than 20 years ago and is used by the main satellite operators
internationally, and it has proven its high degree of reliability in
many different cases.
The following diagram illustrates the concept of
this technique of geolocation, as described below:

The unknown transmitter antenna is aimed at the
interfered satellite, transmitting most of its energy through the main
lobe and a smaller part of its energy through the side lobes, which
reaches adjacent satellites at a very low level.
When the original signal is transmitted to two
satellites that are located in different orbital positions (the
interfered satellite and the adjacent satellite), the signal travels
different distances to reach the two adjacent terrestrial stations to
simulate one single monitoring point indicated on the diagram as
“Receiving stations of both satellites,” which involves a time
difference of arrival (TDOA) on the order of µs.
Likewise, the signal experiences a frequency
difference of arrival (FDOA) on the order of Hz, which is shown by the
Doppler effect generated between the two satellites.
These parameters, TDOA and FDOA, are processed in
the geolocation system and are represented by two lines that,
depending on the satellites used, intersect in an area inside the
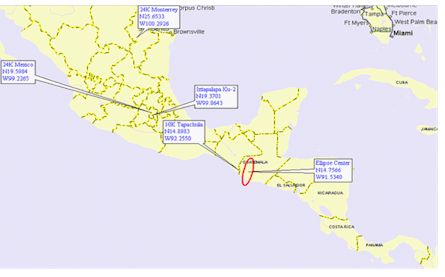
interfered satellite’s coverage, thus tracing an ellipse with central
geographical coordinates that indicate the zone where the terrestrial
station that is transmitting the unknown signal is located.
To achieve this, known signals have to be used to
compare them with the unknown signal, and by a series of
triangulations that the geolocation system itself processes, the
corresponding ellipse, indicated below, can be obtained:
2. Verification of transmission of possible sources of harmful
interferences
Once the ellipse has been obtained, there is a
point of departure inside the satellite coverage to find the
interference, and the following step by the satellite operator to try
to find the source generating this interference is to contact its
customers in the zone to check their transmissions.
In most cases of accidental interferences because
of equipment breakdown or human errors, it is probable that contact by
phone and maybe testing by switching the equipment off and on may
identify the station that generates the interference in order to
subsequently take the relevant remedial actions.
Nevertheless, in the case of unauthorized
transmission being dealt with here, it is difficult to contact by
phone the responsible person in the terrestrial station because the
operator of the terrestrial station shall not accept any
responsibility.
Once the above has been accomplished, the satellite
operators shall report it to the Regulator and shall draw up a
solution strategy, investigating the origin of said unauthorized
transmission. The Regulator shall use its own search methods, with the
participation of the affected satellite operator, who shall be able to
provide technical assistance and human resources with specialized
brigades in detecting harmful interferences.
Verification via horn antennas
In some cases, transmissions from a terrestrial
station can be verified without any physical connection to the
station’s ascending chain, including the possibility of obtaining
samples from said transmissions although from a location outside the
station’s facilities.
This method is illustrated and described below:

This method uses a spectrum analyzer and a horn
antenna operating in the frequency range of interest, which for this
type of verification would be the transmission frequency to the
satellite in the corresponding operation band.
The idea is to be sufficiently close to the
transmitting antenna, whether by land or by air, to be able to receive
the uplink frequency of the interfering carrier or signal that is
present on the satellite and that is monitored on the downlink
frequency by the satellite operator.
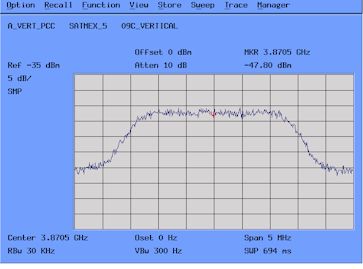
By comparing the spectrum form of the interfering
carrier or signal observed in this verification of transmissions with
the reference chart of the satellite downlink, one can be sure that it
is the transmitting station that one is looking for:

Conclusions
The transmission geolocation and verification
methods described in the present document are reliable enough to help
identify the source generating unauthorized transmissions and
interferences by radiofrequency on satellite communications.
Alonso Picazo
Chair
Sub Working Group on Harmful
Interference to Satellite Systems
|
Additional Information:
Resolution CCP.II/RES. 35(VIII-06).
|
|

