|
Symmetrical algorithms:
These algorithms have only one key that is used
for encrypt and
decrypt. This is shown in the next figure.
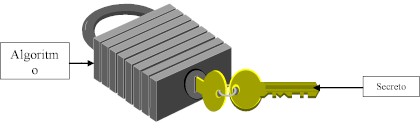
As we said before, the algorithm
is widely known, such as our padlock of the figure,
but only the one who has the key (which is the
secret) can operate it, yellow in our case. As we
can see, the same key is used in both ends.
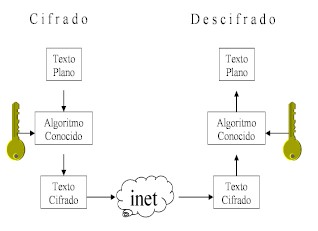
The key length gives the strength
of the symmetric algorithms. Let’s imagine the
example of the key of a padlock. If someone has to
guess the shape of the key without having any clues,
the longer the key, the better. It will have more
variability of teeth and cracks. It is the same with
the informatics concept: the longer the keys are
(more bits), the safer it is. Symmetric algorithms
are very quick to encrypt and decrypt a bunch of
information, and that makes them suitable to encrypt
a complete file, an executable program, or an image.
The great limitation of symmetric algorithms happens
when working with the same key becomes a problem.
Justly, the distribution of the key among people who
wish to operate between themselves supposes that
they meet somewhere or that they have another
confident way for distributing the key. In general,
we say that they are handier in cases 1 to 1, where
only two persons must know the same key. There are
lots of symmetric algorithms –the blocks mentioned
before as "public algorithm" – for example DES,
Triple DES, AES, Blowfish, IDEA among others.
DES algorithm
No doubt, DES (Data Encryption
Standard) is the symmetric algorithm mostly used
until nowadays. It was created in 1974, and the USA
government adopted it as standard in 1977. It became
ANSI standard in 1981 Surprisingly, the original
algorithm proposed by IBM had a 128 bits key, but
the standard adopted, shortened it to 64 bits. The
key is considered a little bit short for the actual
computers. This was demonstrated in 1998, when
different joint people used the brute force method,
and broke it. However, this method is still
considered strong since it hasn’t shown any
theoretical debility.
The DES algorithm codifies plain
text blocks of 64 bits, using a 64 bits key, and
producing a ciphered text of also 64 bits.
Variants of the DES algorithm:
Many varieties have been tried on
the DES algorithm, but they’ve shown very little or
no improvement at all compared to the original. Some
of them have even shown worse behaviors. The most
used DES version is the one that points to solve the
problem of the key length. This variety is called
"Triple DES". On Triple DES, we encrypt with the k1
key, decrypt with k2, and encrypt once again with
k1. The resultant key is the concatenation of k1 and
k2, with a length of 112bits. Next picture shows
this.
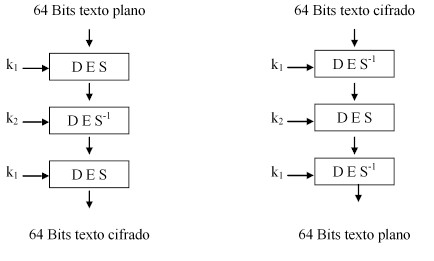
The decryption process is the
opposite. Following the complete sequence of
transformations, we can see that each stage
deciphers what was ciphered with the same key, using
the opposite algorithm, so the plain text is
obtained again at the end.
Symmetric algorithms
cryptoanalysis
DES has motivated different ways
for cryptoanalysis. None of them has succeeded, but
yet they have "professionalized" this activity,
causing successful attacks to other algorithms. The
easiest attack is the so called "brute force". It
simply tries out all possible keys, since one of
them produces the plaintext. Next table shows the
time needed to try all possible combinations.
easiest attack is the so called "brute force". It
simply tries out all possible keys, since one of
produces the plaintext. Next table shows the time
needed to try all possible combinations.

It is then clear, that a key
length of 128 bits or more, makes senseless to try
all keys. On the table we can see the required time
to try all combinations if a cipher is done every
microsecond (a realistic speed nowadays) and if a
million (106) ciphers are done every microsecond
(reachable speed on the near future). It is useful
to note that 109 is equivalent to a 1 followed by
nine ceros.
The two most used schemas are
based in having many plain texts and their
correspondent ciphered ones. Using different keys
each time we use DES –"session keys"-, brings more
security to the algorithm. We will talk about them
now.
Differential cryptoanalysis:
Its principle is to analyze two
ciphered texts coming from two plain texts, which
have special differences between them (number of
bits). The ciphered texts are analyzed looking for
keys that have high probability to produce those
differences. Having analyzed more ciphered texts
pairs, one of the keys will become the most
probable.
Linear cryptoanalysis:
This method is based on making a
logical XOR operation among some bits from the plain
text, and then doing the same, but with a ciphered
text. We make then XOR with both results from
before, obtaining only one bit. If we do this
procedure to many plain-ciphered pairs of texts, we
can see whether we get more zeros or more ones. The
presence of much more zeros than ones, or vice
versa, is used to assign matching probabilities to
the analyzed key.
Néstor Pisciota
Universidad Blas Pascal
|




