The critical telecommunications infrastructure protection model -
previous presented in info@CITEL [1] - is implemented by a set of five
methodologies. Although each methodology is responsible for a specific
part of the model, they are interdependent, since the output of one is
the input of another.

Fig. 1. MI2C phases
Application of MI2C
In the year 2007, the MI2C was firstly used to
define the critical portion of the telecom infrastructure in the
scope of the XV Pan American and the Parapan American Games (Pan/Parapan
2007) that were held in Rio de Janeiro in July and August 2007.
Now, in this second application the scope is the
Brazil as a whole that is the focus of this work.
Phase 1 – Telecommunications services identification
Description: The main objective here is to
identify each and every telecommunications service, considering the
scope of the application.
Application: An internal group was created to
work in a project, where the objective is the participation in
multidisciplinary group discussions to identify all of the
telecommunications services (and the correspondent service providers).
The main source of information is the Law 9472/97 (General
Telecommunications Law) [2].
Phase 2 – Definition of aspects for service evaluation
Description: The aspects that will be used to
evaluate the services identified in Phase 1 are based on three
distinct areas of interest: service users, society and the State;
some of them are quantitative while the others are qualitative.
Application: Meetings were held with Anatel, CPqD,
researchers, telecommunications specialists, information security
specialists and professors, amongst others, to identify the relevant
aspects. Table 1 illustrates the results from this phase.
Table 1. Relevant aspects to be analyzed.

Phase 3 – Definition of aspect criticality levels
Description: In this phase,
the level of criticality (qualitative and quantitative) for each
aspect is defined to allow the analyses of every service defined in
Phase 1. These levels of criticality should reflect the influence of
the telecommunications services for each aspect. There are several
ways to proceed with this definition, from a simple and generic
classification (using 3 levels: high, medium and low), to more
complex classifications (using n levels, where n is
odd) if a greater granularity is required.
Application:
This analysis was performed during multidisciplinary discussion
group meetings with participants from Anatel, researchers,
telecommunications specialists and, information security specialists,
amongst others. Three levels of criticality were defined: “High”,
“Medium” and “Low” (see Table 2).
Table 2. Levels of criticality for the different aspects considered.

Phase 4 – Definition of aspect weights
Description: In this phase the different
scenarios that can take place in a particular country are mapped.
Using aspects weighting it is possible to map not only the real
situation of the country, but also exercise hypothetical scenarios
as well; i.e. it is possible to establish different scenarios by
simply adjusting the aspects weighting.
Application: A group of specialists and analysts
held meetings to assign the aspects weightings. Since there are no
extraordinary events taking place in Brazil, the weights were set to
“1” for all aspects (see Table 3).
Table 3. Definition of the weightings used
to create scenarios.

Phase 5 – Analysis of service criticality levels
Description: This phase is responsible for
analyzing the level of criticality for each telecommunication
service with respect to each aspect.
Application: This analysis was done by
multidisciplinary discussion groups in workshops. Some simple
examples of questions that were discussed are shown below: • Safety
and health aspects: How does the telecommunication service under
analysis influence the health and safety aspect? • How critical is
the service analyzed in the perspective of this aspect? • Does this
service contribute to, assist or facilitate this aspect?
These simple questions were asked for each
telecommunication service identified in Phase 1. All the services
were analyzed from the perspective of each aspect (see Table 4).
This is one of the most time consuming phases of the methodology.
Table 4. Analysis of criticality.

Phase 6 – Mapping of the critical telecommunications
services
Description: The main objective of this phase is
to convert the qualitative values to quantitative ones in order to
prioritize the telecommunication services. The method of calculation
employed can be a simple arithmetic average or Analytical Hierarchy
Process-AHP methodology, or other one method that attains the
desired objective.
Application: At this sample application, High,
Medium and Low were mapped to the values 1, 2 and 3. Subsequently
the calculation was performed and the ranking was defined based on
the average. The results are shown in Table 5.
Table 5. Classification of level of criticality.

Phase 7 – Identification of telecommunications network
infrastructure
Description: Identification of the
telecommunications network infrastructure used by critical services.
Application: Through workshops, meetings, work
sheets, and with the support of the Brazilian telecom operators, the
telecommunications network infrastructure was identified. The
integration between different types of networks, such fixed and
mobile services, must be considered in this phase.
To analyze the answers, a semi-quantitative
approach was used, identifying information such as points that
concentrate traffic and functionalities, long distance strategic
traffic routing and infrastructure sharing, etc.
To support the application of methodology
software has been developed.
Almost 80 types of evaluation criteria were
grouped into 5 categories: Location and Infrastructure (including
electrical power), Transmission, Switching type 1, Switching type 2
and Switching type 3. Table 6 illustrates a sample of the criteria
for each category.
Table 6. Criteria per category.

Adopting this approach (categories vs. criteria)
serves a twofold objective: a) to minimize the presence of mistakes
due to answer interpretation (its can happen because of all the
answers was get via telecommunication operators) and b) to minimize
the number of criteria comparisons.
Phase 8 – Mapping of critical telecommunications
infrastructure
Description: In this phase the network
infrastructure used by each and every critical service is mapped in
order to define the critical telecommunications infrastructure.
Performing this phase also requires an in-depth knowledge of the
telecommunications field and the relevant equipment that supports
the services. The required information was obtained through
workshops, questionnaires and study groups that included
telecommunications specialists and the people responsible for the
critical service that is being analyzed. In this phase the level of
granularity can be adjusted according to one’s needs. The critical
network infrastructure found can be detailed at a high level (e.g.
building level) or a low-level (e.g. board level). Either way, all
critical services should always be included in the critical
infrastructure.
Application: The first step of is to attribute
weights for each category in the model formulated in the previous
phase. Fig. 2 shows the natural top-down
approach for prioritizing the categories by importance: the base of
the pyramid (infrastructure) has the highest weighting since, if it
fails, all the categories above it will also fail. The weights and
normalization factors adopted for each category are presented in
Table 7. The normalization factor was introduced into the model to
eliminate the distortion caused by different categories having
different numbers of criteria.

Fig. 2. Top-down approach to prioritize the
categories.
Table 7. Weights and normalization factor per
category.

To obtain the final scores, needed for the
prioritization of the sites, the following formula was used:
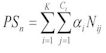
Where:
PS= Final score of the site
K = Number of categories
C = Number of criteria in category
N = Score attributed for the criteria j of
category i
alfa = Normalization factor used for
category i
Results
Table 8 shows (for example) the 10 (ten) highest
ranked stations among all stations analyzed. This information allows
a more efficient resource allocation for infrastructure protection.
For security reasons, the real names of stations and
telecommunication provider have been omitted. Table 8. Top ten
stations ranked.

Conclusions
The importance of critical telecommunication infrastructure
identification cannot be underestimated, since is the first step to
an effective infrastructure protection program. For this reason, it
is important to use a systematic
approach – like the one
embodied in
MI²C – to correctly identify
the most critical parts of the telecommunication infrastructure.
This article has presented the application of the Methodology for
Critical Infrastructure Identification (MI2C) in the
scope of Brazil.
|
Regina Maria De Felice Souza
Anatel |
Sérgio Luís Ribeiro
CPqD |
Christiane Maria da Silva Cuculo
CPqD |

